Stop Building Your Platform Around Kafka
Before you get the wrong idea, I’m a big fan of Kafka. It does a great job but all too often it’s setting your architecture up for failure...

Michael Pollett
Bio LinkedIn DNS CAA Tester Domain Registry

Before you get the wrong idea, I’m a big fan of Kafka. It does a great job but all too often it’s setting your architecture up for failure...

This has since been added , see their latest implementation advice . — For posterity: AWS have made it fairly clear that they’re still not supporting DNSSEC in Route53, so let’s run through the options available...

Here I talk about the implications of building your own serverless architecture, why you might do it, and in particular the security concerns that come with that. Useful for everyone is where we talk about how you’re already using serverless, i...
docker, development, continuous-integration, security, serverless
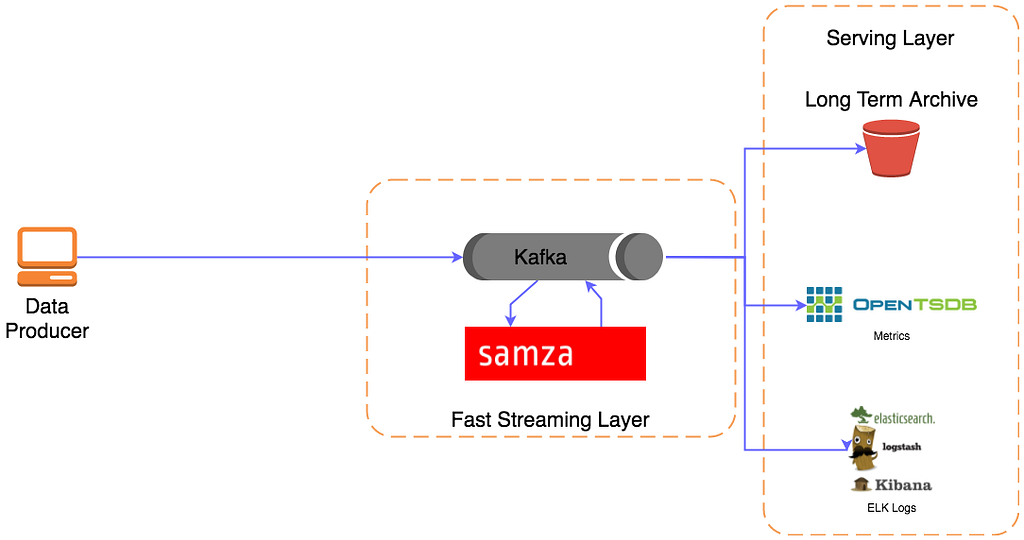
Building reliable events systems As you start to think about whether you need an event or real-time streaming platform, everyone starts in a similar place: Kafka, Samza, OpenTSDB, ELK just for illustration here — a common example but have many alternative and comparable options. This is both a great and the most natural place to start so you’ve not gone wrong yet, but you will quickly discover that this isn’t necessarily the perfect solution...

A recent talk about how we use Docker at DataCamp to provide a serverless architecture for our users to learn data science. Not necessarily a perfect talk, but it digs into the security implications of building such a serverless environment and allowing users to execute code in it...

Why a “503: Slow Down” response from Amazon S3 can actually be good for you! The official AWS S3 docs on Request Rate and Performance Considerations for S3 clearly state, Amazon S3 scales to support very high request rates...
Now although many sites rarely sees 2billion hits a month or 1000 hits per second, why should they not be capable of this, although the direct correlation is loose, with concurrency can come speed. Speed in this sense is possibly even serving a page to a single user at a time but why not do it in a decent timeframe...
My latest exploits have involved writing an apache module so let’s look at a basic getting started guide for developing apache modules. Requirements This assumes running on a RHEL platform with httpd-dev installed...